
IT-Security-Monitoring in real time
Accelerate your Cyber Resilience Status without effort
Hackers scan the Internet for vulnerable systems every hour. At the same time, the number of new vulnerabilities published every day is increasing rapidly.
What use are temporary pentests? The result is outdated the next minute.
Automated security audits regularly check your company-wide IT landscape in real time. For compliance, audits and reporting you have a lot of critical information at hand.
Keep an eye on the situation. Identify potential vulnerabilities immediately and are able to take proactive action. In the event of security-critical changes, the notification function automatically sounds the alarm and takes you directly to the findings. This accelerates the optimization process and permanently minimizes risks.
Measure and prove IT security
through continuous monitoring of enterprise-wide IT infrastructure
Proactively reduce attack surfaces
through prioritized recommendations for action and functions that significantly accelerate the security process
Detect anomalies and differences immediately
through automated notifications and differential functions
Evaluate and compare the IT security situation
using valid, traceable key performance indicators (KPIs) and optionally bookable benchmarks
Individual reports for management and IT
with graphically visualized overview for management and detailed information for IT
security managers
Meet security & compliance requirements through continuous risk management of suppliers and business partners
The potential for misuse is growing, new attack surfaces are emerging. Knowing this is important – and it needs to be brought more into public awareness. Only those who know and recognize possible dangers are able to make the right decisions and take appropriate measures to protect themselves and others.
BSI Cyber Security Situation Report · Germany 2023
Checkdone IT offers IT security monitoring. Automated reports show at a glance how your IT security and that of your business partners is doing in terms of network, application & web security, encryption, infections, data leaks & configurations. This increases transparency, reduces risks and helps to implement supplier risk management in a resource-efficient way.
Checkdone IT provides up-to-date, KPI-based analysis of the external IT security posture of organizations of all sizes. The security assessments, which are conducted according to international industry standards, help to identify critical problems at an early stage.
Thanks to the user-friendly SaaS platform, companies can easily check and manage their own IT security as well as that of their investments and business partners – even without cybersecurity expertise!
With ISO 27001 certified network and data center partners in the EU, Checkdone IT offers highest data security.
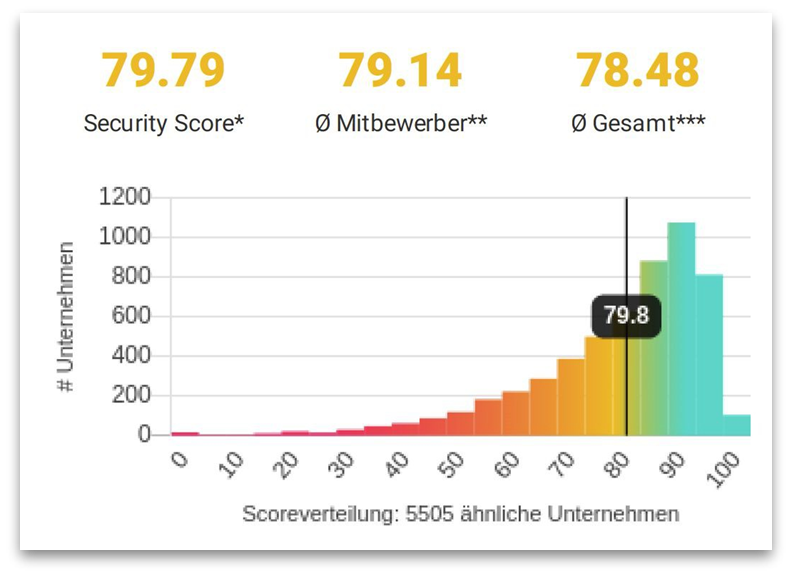
The Cybersecurity Score
Automated security data is evaluated according to international industry standards and forms the security score. It shows from an external view, how secure the company-wide IT infrastructure is. The results are clearly presented in an interactive risk analysis report.
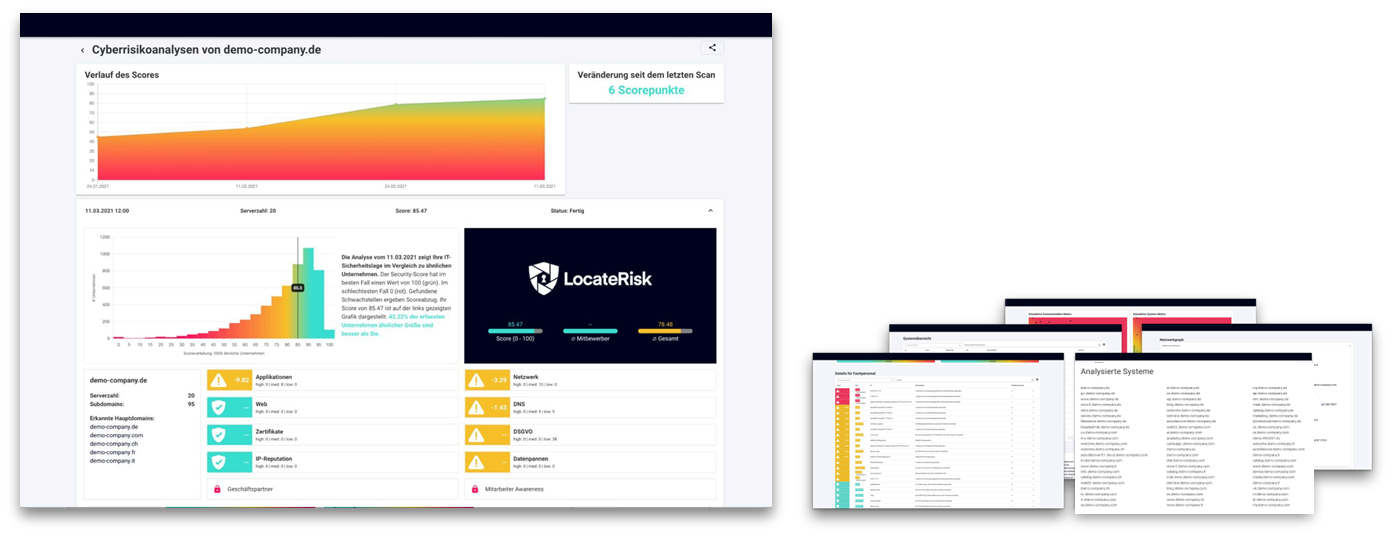
The interactive IT Risk Report
IT managers receive a detailed list of critical findings, including recommendations for remediation.
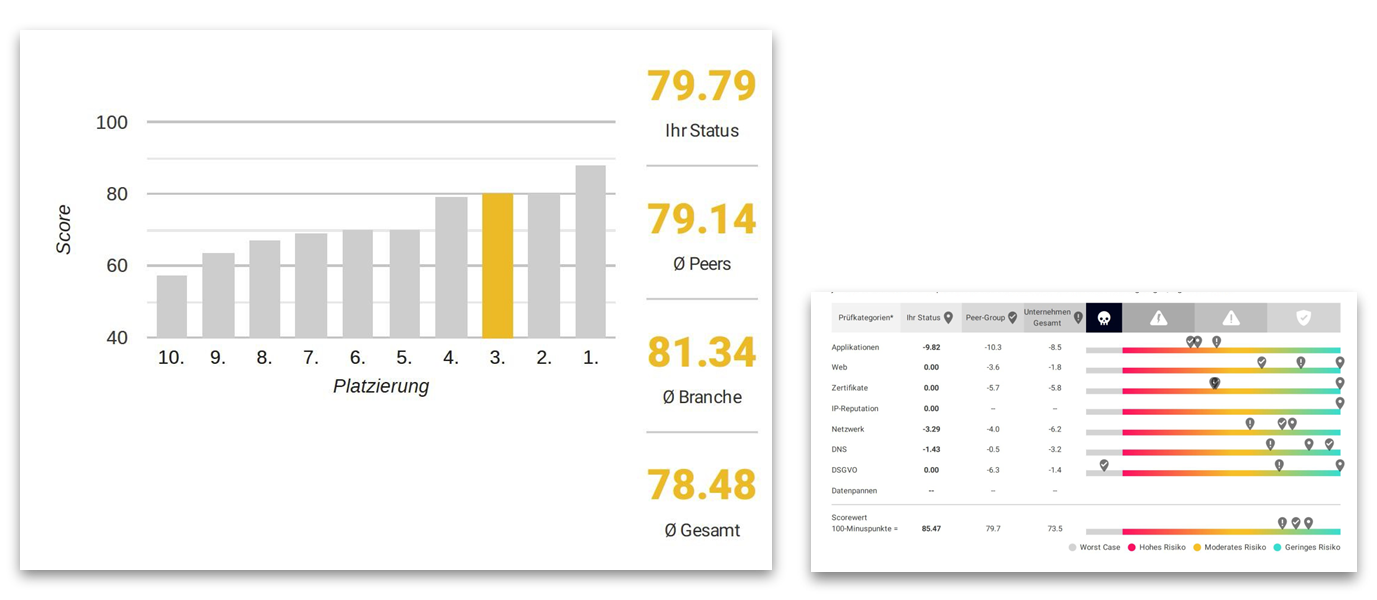
The Cybersecurity Rating
The chart shows how the enterprise- wide IT security compares against up to 10 Competitors/partners/partners of your choice.

The Management Report
The report provides the management level with an easy-to-understand overview of the security posture.

