Check Point Software Technologies is a leading provider of cyber security solutions to corporate enterprises and governments globally. Check Point Infinity’s portfolio of solutions protects enterprises and public organisations from 5th generation cyber-attacks with an industry leading catch rate of malware, ransomware and other threats.
Established by CEO Gil Shwed in 1993, Check Point introduced FireWall-1, the IT industry’s first stateful inspection firewall technology. Over a quarter of a century later, Check Point’s ground-breaking technology remains the gold standard for network security, and the company has continued to deliver innovative cybersecurity solutions.
For the last three decades, Check Point Software Technologies has set the standard for Cyber Security. Our mission is to secure your everything. Across the ever-evolving digital world, from enterprise networks through cloud transformations, from securing remote employees to defending critical infrastructures, we protect organizations from the most imminent cyber threats.
With Check Point Infinity, the only consolidated cyber security solution across cloud, networks, endpoints, mobile and IoT, we are continuously pioneering cyber security innovation with the most advanced AI-based threat Intelligence and prevention technologies, unified security management, and cloud security automation to help protect organizations from 6th generation of cyber attacks.
With over 6,000 security experts, a world-acclaimed research and intelligence unit, and the broadest ecosystem of business and technology partners, we protect over 100,000 organizations of all sizes across all industry verticals in 88 countries to achieve allow better experiences for in a safer digital world.
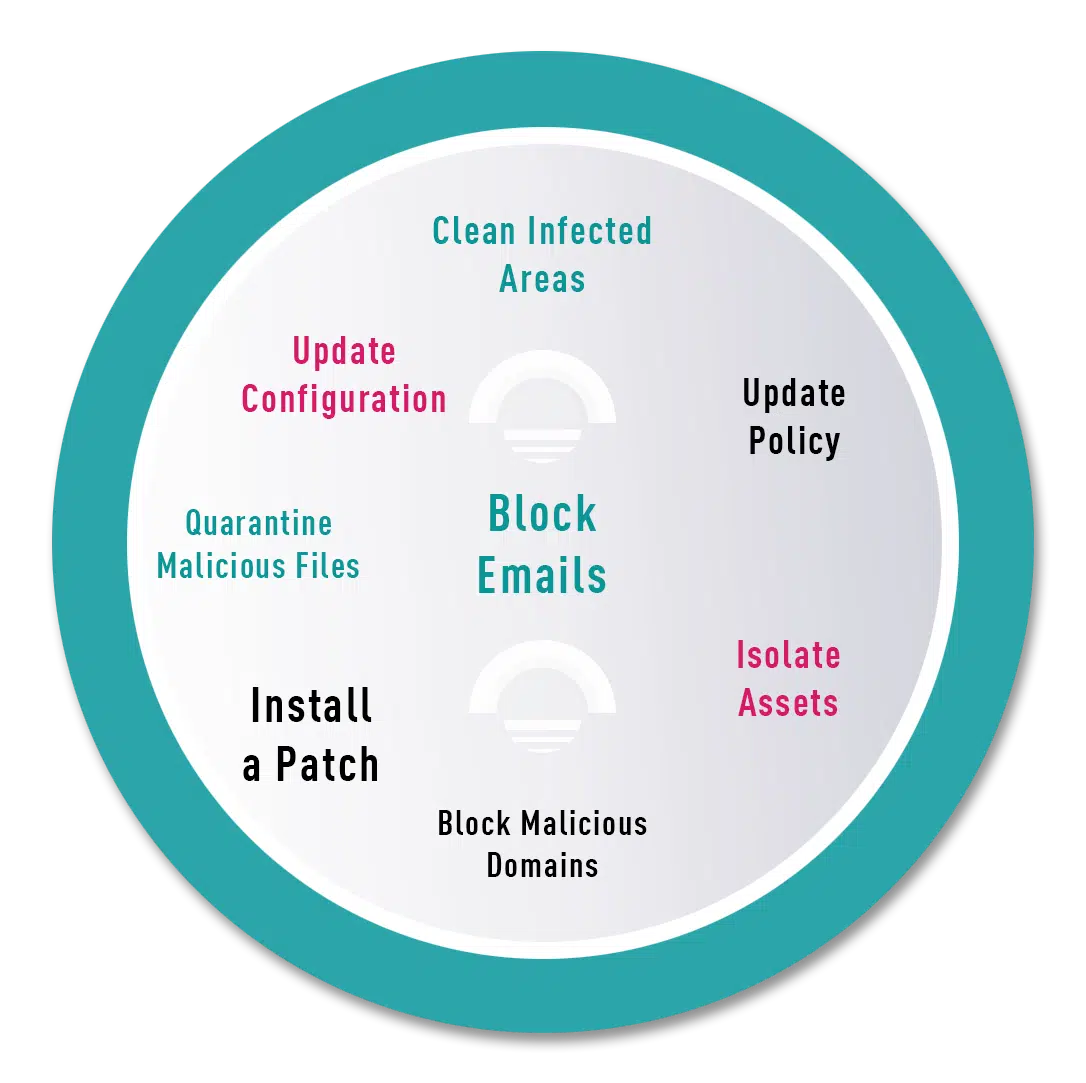
Check Point Incident Response Team (CPIRT) offers 24/7, data(Intelligence)-driven, and vendor-agnostic incident response services. The CPIRT global team helps our customers manage, mitigate, and understand active cyber incidents. The team helps customers of all sizes prepare for cyber incidents through proactive services; such as Playbook Development, Tabletop Exercises, and Threat Hunting.