IT and security teams have good reason not to trust the public Internet. Phishing and malware accounted for 39% of all data breaches in 2020, a Verizon report found. And a Forrester Consulting study commissioned by Cloudflare found that in 2020, 61% of companies with more than 1000 employees experienced an increase in phishing attacks compared to previous years.
Every IT and security professional wants to keep their organization from being included in these statistics.
Specifically, they want to:
-
Block malware and phishing, which constantly shift tactics to evade detection.
-
Stop data loss in general, whether via infected devices or user interactions.
-
Get better visibility into employee Internet browsing, in order to understand their organization’s specific threat landscape and respond faster to breaches that do occur.
These use cases are important elements of Zero Trust security, in which Internet properties and code should not be implicitly trusted — and must therefore be securely processed at the moment of user interaction.
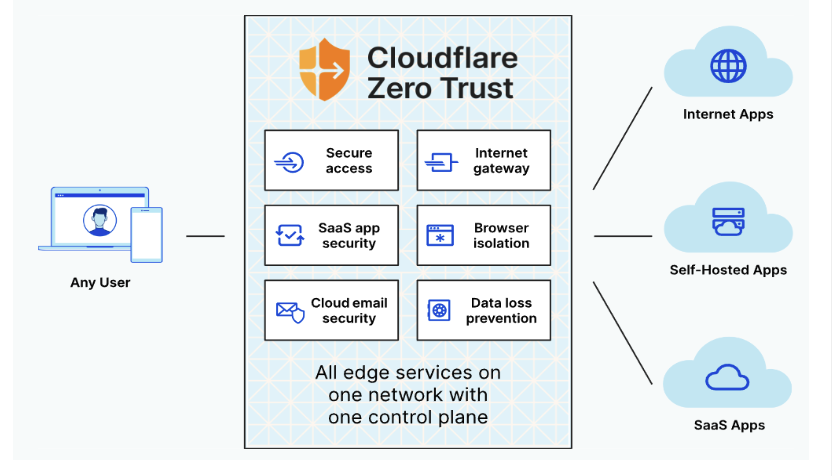
In order to accomplish these goals, some organizations are turning to browser isolation, in which employee Internet browsing is kept separate from local networks and infrastructure.
Implemented thoroughly and efficiently, browser isolation shows potential to be the single most powerful way to mitigate attacks coming from the Internet. Unfortunately, it has so far remained a niche technology because of a number of challenges — including high costs, poor browsing experiences, logistical management hurdles, and security gaps.


