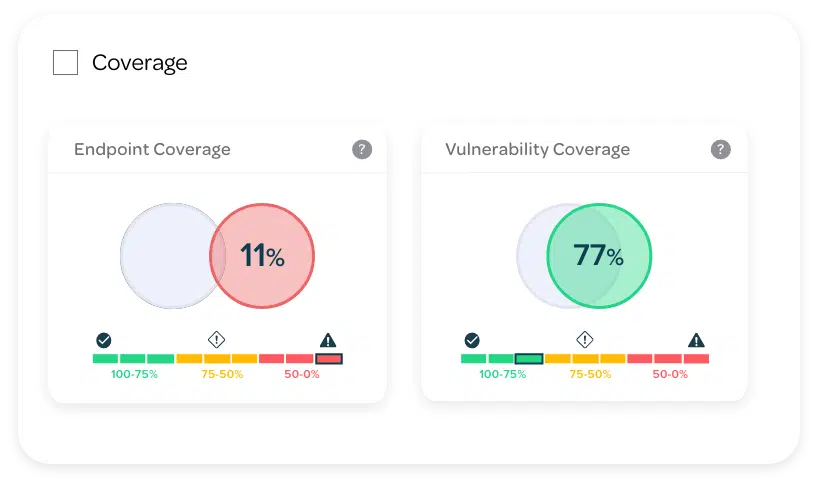
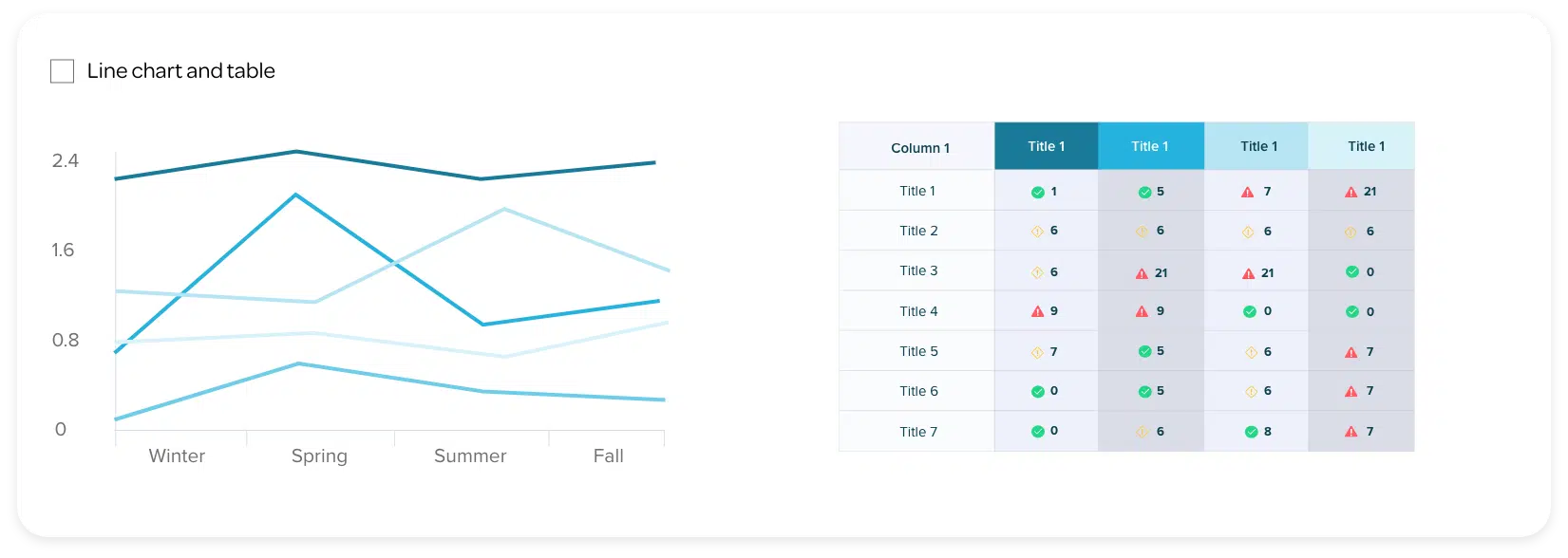
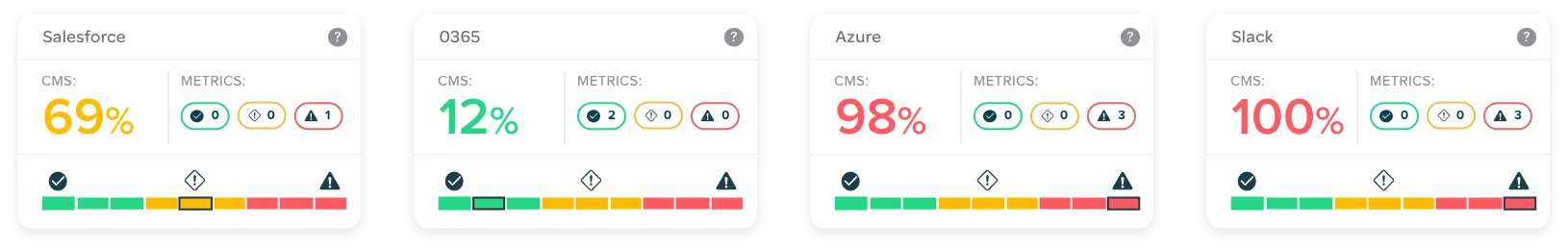
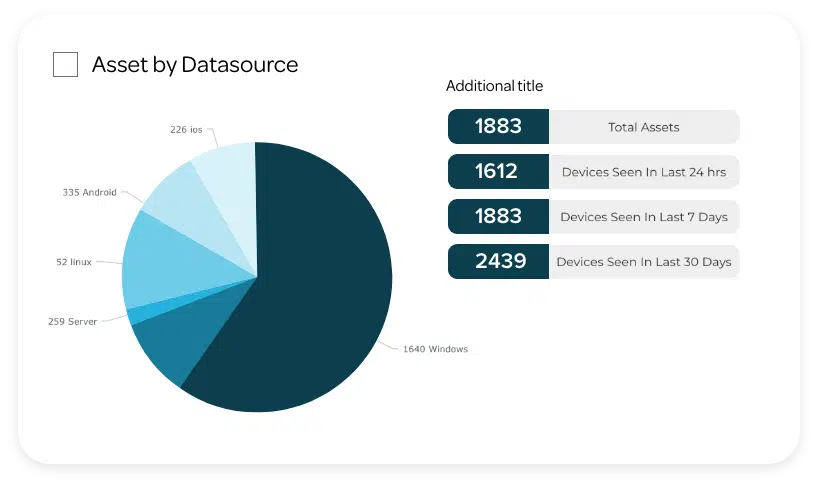
Our Continuous Controls Monitoring (CCM) platform allows you to see and understand your security and risk posture in real time. You get complete controls visibility with automated, continuous monitoring of all your security controls, continuous compliance, whilst benefitting from our unique service wrap.
Get more, see more, achieve more
What you get
Real-time security assurance and peace of mind
Get security assurance and peace of mind through accurate real-time data from all your controls, with early awareness of potential problems – all via a managed CCM platform that includes ongoing service from Quod Orbis experts.
What you see
The complete security and risk picture, all in a single source of truth.
See customised and personalised visual controls status 24/7 from across your organisation via a configurable, user-friendly dashboard that’s as relevant for CxOs as it is for IT, security, risk, audit and compliance roles.
What you achieve
Continuous compliance, increased cyber resilience, reduced risk and cost
Achieve automated assurance and continuous compliance status in real time – all with significantly reduced risk and cost for protection of your business operations, revenue, reputation and profits.
Any framework, any control
Compliance with all major frameworks, standards and regulations
Quod Orbis CCM enables faster, easier organisational awareness and compliance with all major international security frameworks, standards and regulations.
The QO service wrap
Our Service Wrap provides your business with the agility and flexibility to continuously evolve with you as you need it, by maintaining accuracy in the platform so you have 100% confidence in the information you view.
Benefits of our Service Wrap with our CCM Platform include;
- Access to controls experts
- Your own Customer Success Manager
- Ongoing updates
- QO experts monitoring your platform
We scope, we onboard, we support, continuously.
What is CAASM (Cyber Asset Attack Surface Management)?
Cyber Asset Attack Surface Management (CAASM) is a relatively new, emerging technology that identifies, monitors and manages the potential points of entry or vulnerability within an organisations digital infrastructure that could be exploited by cyber attackers. The “attack surface” refers to all the entry points, interfaces, systems, and components that can potentially be targeted by malicious actors.
As the attack surface is now evolving and increasing exponentially, coupled with rapid digital transformation, it has never been more imperative to fully understand your attack surface. However, this has become challenging in recent years, particularly for larger enterprises that have moved to the cloud and now have a mix of cloud, on-prem and potentially legacy tech and could be struggling to understand exactly what assets they have in their inventory to really comprehend what their potential attack surface is. Couple that with the progression in more flexible and hybrid working and BYOD has meant that it has become truly challenging for cyber security teams to fully be proactive in their cyber security architecture. Enterprises will remain vulnerable to attacks if they do not address the visibility they have of this limitless attack surface, because, frankly, keeping processes and policies the same, simply no longer cuts it.
Why do you need CAASM?
CAASM addresses this issue by supporting businesses in creating a live asset repository and a series of proactive measures to reduce an organisations attack surface and enhance its overall cybersecurity posture. Gartner further validates this with their latest Hype Cycle 2023 for Security Operations. By implementing a CAASM solution your organisation will ultimately significantly reduce its threat landscape because you will have a full understanding of assets, be able to review – in real time – your technology infrastructures risk levels and therefore be able to be considerably more proactive and reactive to cyber threats.
What are the benefits of CAASM?
Real-time, automated viewpoint of your Security Posture: Our CAASM solution helps organisations gain a clearer understanding of their digital attack surface, including all potential entry points that could be exploited by attackers. By identifying and addressing these vulnerabilities, organisations can significantly improve their overall security posture.